I'll leave the detailed version to hasherezade :)
This is a quick look at what the malware is about and what functions it uses.
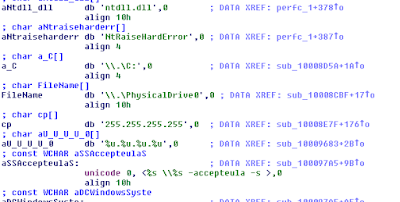
Looks for physical drives on the infected computer.
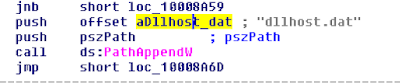
dllhost.dat > PsExec
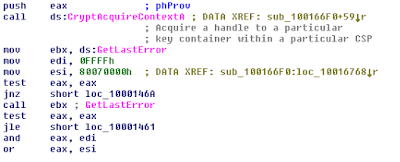
Provider: MS RSA AES
Running PSExec on the entire subnet, after accepting the EULA of course :)
Extensions to be encrypted.
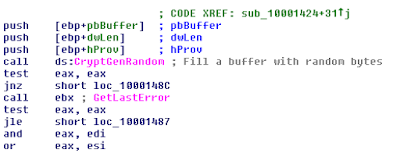
Encryption part.
And here are all the encryption functions that are called.
This is a quick look at what the malware is about and what functions it uses.
Looks for physical drives on the infected computer.
Here's the bundled-in psexec, as dllhost.dat:
Here's another PE, looks like used to launch the runndll32.exe as perfc.dat:
Infection starts.
dllhost.dat > PsExec
System restart.
Encryption.
Provider: MS RSA AES
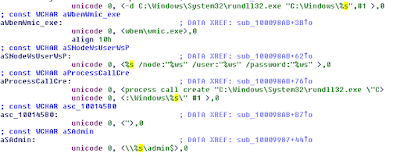
This is where it starts in user-land.
All the familiar messages.
And here's all the WMI stuff.
Also, note that rundll32.exe is called by '%s' - perfc.dat in this case.
Running PSExec on the entire subnet, after accepting the EULA of course :)
Extensions to be encrypted.
Looks out for the extensions it wants to encrypt (hard-coded, different to the ones seen earlier in Petya mid-2016).
And here are all the encryption functions that are called.
Like I said earlier, this is a quick look into the malware not a detailed analysis. But it should give you some insight into how it works.






















No comments:
Post a Comment