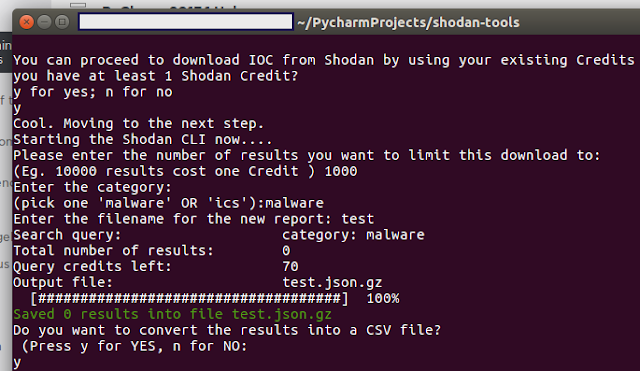
This is a small script that converts the CSV downloaded from Shodan into a new CSV that is usable for ingesting into other platforms (eg. ThreatConnect etc). You can grab the IOCs column (eg. IPs) and create a new csv file with just that column - this new CSV can then be ingested into any other platform. You can pick and chose what column(s) you want to carry over into the new CSV - minor tweaks would be required. I'll keep updating this script and make it as interactive as possible - watch the gitHub repo!
Get it here.
Get it here.