PsExec can be used quite easily on any network to move laterally from one system to another. Here's one way of detecting lateral movement.
Demo:
We'll create a PsExec session and then look for the events and note them down. These can then be used for monitoring alerts or forensic investigations.
Launch a PsExec session from one machine to another and note the time:
Machine A -

Session launched on Machine B -
Now we look through the Windows Events Viewer and find the events for this session.
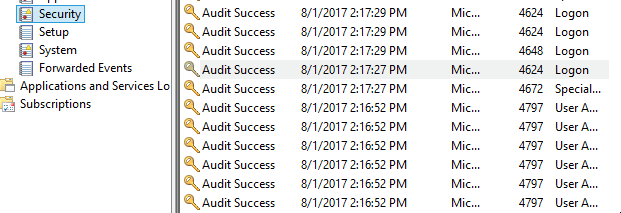
Looking through the Security events, we can see in the image below the Logon event (ID 4624) was created for the session that we launched (note the timestamp).
Details of the event should give us more information on the event.
This tells us clearly that the logon was from our Machine A, through PsExec:
Next, we need to look for the service that was created as part of this session. PsExec creates the process PSEXECSV.exe on the host system when successfully launched. 

In order to find that the process created on this host system (Machine B), we need to look under the System events.
Look at the details:
These are the events you need to monitor/investigate for PsExec execution on the host systems. The whole process can be automated through a SIEM for passive monitoring for security events or can be executed ad-hoc as needed for investigations and incident response.
When investigating systems post-incident, you can acquire the events files at this location in Win8* :
C:\Windows\System32\winevt\Logs
Once acquired, these files can be reviewed in the Windows Events Viewer on your investigation machine.
:)







No comments:
Post a Comment