The
downloader comes as a Microsoft Office doc - word or excel, with Macro code.
Upon
macro enablement, then VB code is executed and the payload is downloaded and
executed.
Flow:
- Downloader execution - document is opened in word or excel
- The Macro-code is enabled and executed
- Script makes a call to download the payload from the internet
- Encrypted payload is downloaded
- Payload is decrypted using the running XOR key
- Decrypted payload is saved as a different file and then executed
Step by
step analysis:
Declarations >
Public MarkusPils() As String
Public BladeRunner_4 As String
Public Const BladeRunner_System = "User-Agent"
Public SubProperty As Object
Public BladeRunner_VEAM As Object
Public BladeRunner_Fish As Integer
Public AlertN() As String
Public AlertNE As String
Public BladeRunner_PokerFace As Variant
Public BladeRunner_aifde As Object
Public BladeRunner_FLAME As String
Public BladeRunner_avatar As Object
Public smbi As String
Public BladeRunner_2 As String
Public Const Quubo = 0
Public Stocke As Integer
Public BladeRunner_Project As String
Public C2H5OHName As String
Public BladeRunner_PathTo2 As String
Public CofeeShop As Object
Declarations >
Public MarkusPils() As String
Public BladeRunner_4 As String
Public Const BladeRunner_System = "User-Agent"
Public SubProperty As Object
Public BladeRunner_VEAM As Object
Public BladeRunner_Fish As Integer
Public AlertN() As String
Public AlertNE As String
Public BladeRunner_PokerFace As Variant
Public BladeRunner_aifde As Object
Public BladeRunner_FLAME As String
Public BladeRunner_avatar As Object
Public smbi As String
Public BladeRunner_2 As String
Public Const Quubo = 0
Public Stocke As Integer
Public BladeRunner_Project As String
Public C2H5OHName As String
Public BladeRunner_PathTo2 As String
Public CofeeShop As Object
Grabs all
the variables from the doc properties >
And you can also see this in the properties window, under Status:
The variables extracted from the properties are then used as Array values for 'AlertN' >
C2H5OHName
: "Microsoft.XMLHTTP" : String : Asck.PropellersHead
Insert
BreakPoint >
CofeeShop
: : Object/IServerXMLHTTPRequest2 :
Module2.C2H5OH
smbi :
"rundll32.exe
" : String : Module2.C2H5OH
AlertN(2)
: "shell.Application"
: String : Asck.PropellersHead
BladeRunner_avatar : : Object/IWshShell3 : Module2.AnimTransferMap
Shtefin has three URLs hard-coded, they will all be called in succession if the previous one fails.
Shtefin :
"fondazioneprogenies.com/38rh76fCHASluxurious-ss.com/38rh76fCHASurban-dna.pt/38rh76f"
: Variant/String : Module2.AnimTransferMap
URLs from Stefan are passed into MarkusPils as array values:
URLs from Stefan are passed into MarkusPils as array values:
Stocke :
6 : Integer : Module2.C2H5OH
BladeRunner_FLAME
: "C:\Users\RAGNAR~1\AppData\Local\Temp" : String : Module2.C2H5OH
LBound is 0 and UBound is 2 - which means that the URLs will be picked through a loop, 1 to 3:
If the server gives anything other than a 200 response code, it'll through an error and move to the next URL. If not, that means the download was successful and it'll move on the next routine.
'ShugarMilk' is given the value of 64 above - this will translate into 'e', which needs to be less than 300 in order to execute the program to get the desired output:
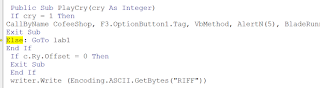
PlayCry 1 and PlayCry 2 execute different parts of the code:
PlayCry = 1
This will execute:
PlayCry = 2
This will take the 'Else' statement and execute a different part of the code, at lab1:
'sinus' is where all the downloaded data is processed:
BladeRunner_FLAME :
"C:\Users\RAGNAR~1\AppData\Local\Temp" : String : Module2.C2H5OH
BladeRunner_PathTo2 :
"C:\Users\RAGNAR~1\AppData\Local\Temp\hromberght8" : String : Module1.mapRender
More processing:
BladeRunner_Project
: "C:\Users\RAGNAR~1\AppData\Local\Temp" : String : Module1.mapRender
The file is being loaded:
And now the data will be decrypted, using the running XOR key as shown below:
These are the events that are executed from here on:
- Function WidthA will be called
- Dbbb is the file loaded as the encrypted payload (hromberght8)
- Dbbb is opened as bbb, for binary operations
- Gbbb will be ReDim - reading the bbb file from 0 To LOF (complete file)
- bbb will be saved as Gbbb
- PuWord function will now be called, which will have the Gbbb() and decryption key
- bbb will be PUT in Gbbb() for decryption and function WidthA will be called at this point
- bbb will now be GET from Gbbb() - this is the decrypted version - as be
- WidthA will process the file bbbJ (write it to disk as amigobro8.exe)
- This new file is the decrypted payload - ready to execute.
ltwo :
"zueVXBTjygBR8akj5duCwSYO1jxEfnjh"
: String : Module3.PuWord
This is
the KEY that will be used to decrypt the payload (running XOR)
vbFromUnicode
: 128 : Long : Module3.PuWord
The loop
terminates when the file is completely decrypted (end of file). At this point
the decrypted payload is dumped on the filesystem >
This is
the actual malware - TrickBot in this case.
Enjoy and share!
Sample details:
MD4: b71b9f3126883b6a9faa1713e3dc3339
MD5: 7e0237a65a357899116d334df3de4831
SHA-1: 3553f5de61c222f271546087018cc32bcafd6d5e














































No comments:
Post a Comment